Maximizing ROI for Regulatory Compliance and AI Model Training
Today organizations face constant pressure to safeguard customer information while navigating a maze of regulatory requirements. Compliance is not...
5 min read
Victoria Kingsley Jul 29, 2024 8:53:01 AM
The significance of contact center data management and protection is more pronounced than ever. As contact centers handle increasing volumes of complex data, a thorough understanding of data classification and privacy is essential. This blog post delves into the complexities of data classification, focusing on key types of sensitive information: Personally Identifiable Information (PII), Payment Card Information (PCI), Protected Health Information (PHI), Nonpublic Personal Information (NPI), and Material Nonpublic Information (MNPI).
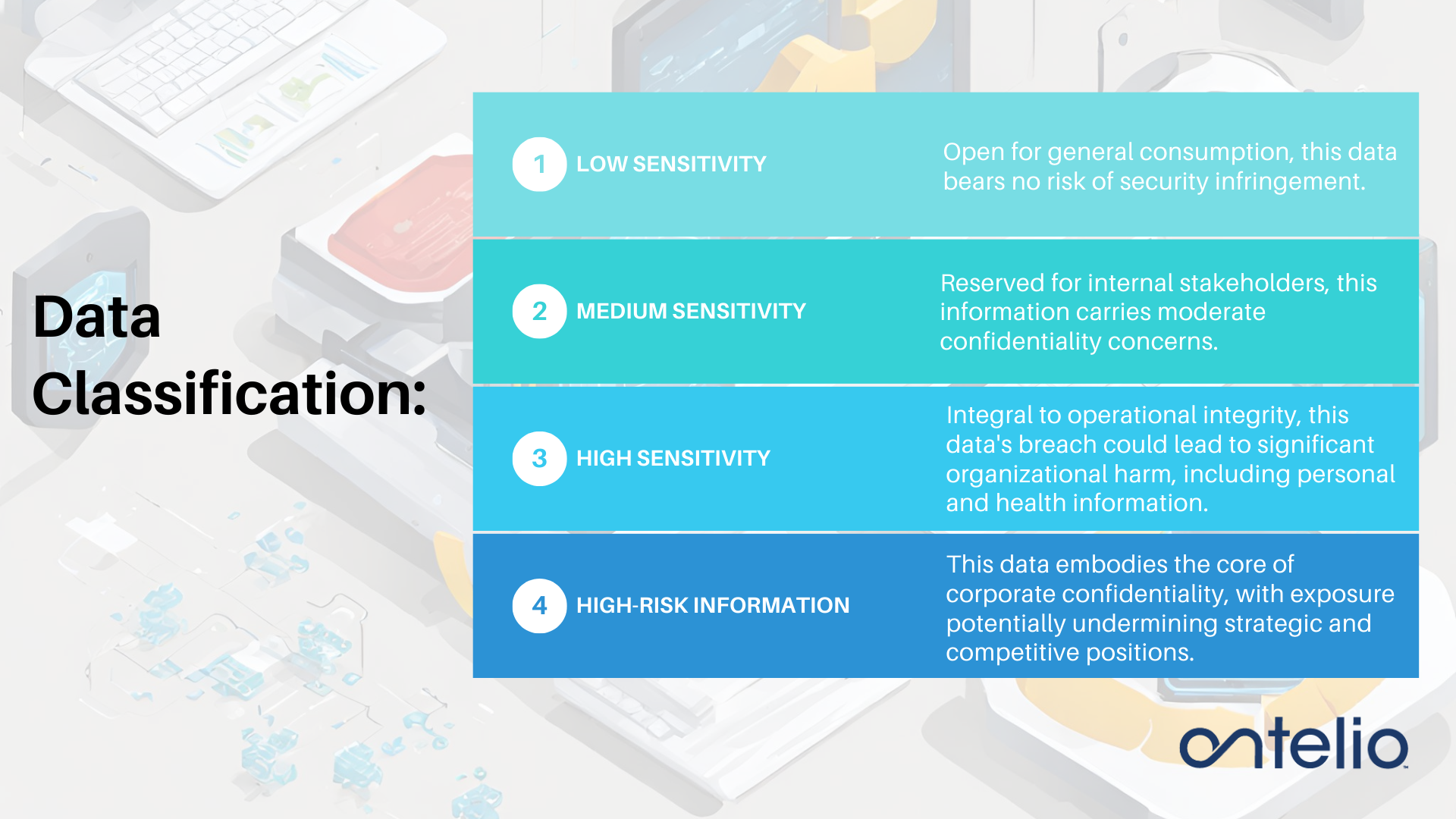
Data classification is the systematic categorization of data based on its sensitivity and strategic importance within an organization. This process involves identifying, labeling, and controlling data to ensure that sensitive information is adequately protected while enabling authorized access to nonsensitive data. The key components of data classification include data identification, data labeling, and access control mechanisms.

Data Identification: This entails the comprehensive identification of various data types an organization handles, such as personal data, financial records, intellectual property, and more.
Data Labeling: Properly assigning labels or tags to data based on its classification, such as “Confidential,” “Sensitive,” or “Public.”
Access Control: Implementing stringent access controls to restrict who can view, modify, or share data based on its classification.
Effective data classification forms the bedrock of a robust data protection strategy, ensuring regulatory compliance and efficient data management.
Data classification is integral for several compelling reasons:
Risk Mitigation: Identifying and safeguarding sensitive data significantly reduces the risk of data breaches and their associated consequences, including financial losses and reputational harm.
Compliance Mandates: Many data privacy regulations, such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Health Insurance Portability and Accountability Act (HIPAA), require organizations to classify and protect sensitive information. Noncompliance can lead to substantial fines and legal repercussions.
Efficiency in Data Management: Data classification streamlines data management processes, simplifying data retrieval, storage, and security. This operational efficiency contributes to informed decision-making and organizational effectiveness.
Cost Optimization: By focusing security efforts on high-risk data, organizations can allocate resources judiciously, minimizing the overall cost of data protection.
Effective data classification presents unique challenges:
Volume and Variety: Organizations grapple with vast volumes of data in diverse formats, from structured databases to unstructured documents and emails, making classification efforts daunting.
Data Location: Identifying the precise location of data across an organization’s network, including on-premises and cloud environments, can be a complex task. Data often resides in various repositories, complicating inventory management.
Evolving Landscape: Data classification must evolve to keep pace with changing data types and regulatory landscapes. Data constantly evolves, new regulations emerge, and business processes change, necessitating ongoing classification efforts.
PII encompasses any information that can uniquely identify an individual. This category includes:
The protection of PII is critical due to its potential misuse in identity theft, financial fraud, and other malicious activities. Organizations must implement comprehensive security measures, such as encryption, access controls, and regular audits, to protect PII. They must also comply with global privacy regulations like GDPR in Europe and CCPA in California, which set stringent guidelines for PII handling. The challenge lies in balancing the need for data accessibility with the necessity of data protection, ensuring that PII is used responsibly and ethically.
PCI includes information related to credit and debit card transactions. This sensitive data category demands high security due to its direct connection to financial resources. Unauthorized access to PCI can lead to significant financial losses for individuals and reputational damage for organizations. Compliance with the Payment Card Industry Data Security Standard (PCI DSS) is mandatory for all entities handling cardholder data. PCI DSS outlines stringent security measures, including network security, access control measures, and regular security assessments, to ensure the protection of cardholder data.
PHI involves any information in a medical record or related to health status that can be linked to an individual. This includes:
The sensitivity of PHI lies in its personal nature and the potential for misuse in discriminatory practices. The Health Insurance Portability and Accountability Act (HIPAA) in the United States mandates the protection of PHI, requiring healthcare providers and their business associates to implement physical, network, and process security measures. The challenge with PHI is ensuring that it remains accessible to healthcare providers for patient care while protecting it from unauthorized access or breaches, a balance that is crucial for both patient privacy and health outcomes.
NPI is confidential information provided by a consumer to a financial institution or obtained in connection with a financial product or service. It includes:
Protecting NPI is essential for maintaining consumer trust and preventing financial fraud. The Gramm-Leach-Bliley Act (GLBA) in the United States governs the disclosure and protection of NPI by financial institutions. This act requires financial institutions to inform customers about their information-sharing practices and to implement measures to safeguard sensitive data. The key challenge in protecting NPI lies in the vast amount of data that financial institutions handle and the varied sources from which it is collected, making comprehensive data management and security a complex task.
MNPI is confidential information about a company that could influence investment decisions. This includes:
The misuse of MNPI, such as in insider trading, can compromise market integrity and investor confidence. Regulations like the Securities Exchange Act of 1934 in the United States enforce strict rules against the illegal use of MNPI, ensuring market fairness and transparency. The challenge with MNPI is maintaining confidentiality while ensuring that all stakeholders, including employees and insiders, understand and comply with the legal and ethical boundaries regarding its use.
Data privacy regulations exert a profound influence on how organizations manage and safeguard data. These regulations, designed to protect individuals’ privacy rights, impose stringent requirements on organizations and hold them accountable for data protection.
Legal Obligations: Organizations bear legal responsibility for safeguarding individuals’ personal data and adhering to specific regulatory mandates outlined in regulations like the GDPR, CCPA, and HIPAA.
Fines and Penalties: Noncompliance with data privacy regulations can result in substantial fines and penalties, inflicting severe financial repercussions on organizations.
Reputation Management: Data breaches and privacy violations can tarnish an organization’s reputation and erode trust among customers, partners, and stakeholders.
The GDPR, instituted in the European Union, serves as a global benchmark for data privacy regulations. GDPR introduced stringent requirements pertaining to data protection, consent management, and breach notification. Its principles have profoundly influenced data privacy regulations on a global scale.

Effective data classification is foundational for robust data privacy and security strategies for contact centers. By understanding and categorizing sensitive data, contact centers can tailor their security measures to provide appropriate levels of protection. This not only aids in regulatory compliance but also enhances customer trust and safeguards the organization's reputation.
Navigating the complexities of data classification and privacy is a dynamic and ongoing challenge for organizations. Understanding different types of sensitive data and their specific protection requirements is crucial in developing a comprehensive data protection strategy. As data continues to be an invaluable asset, its careful management and protection remain of utmost importance.
In today's data-centric environment, Contact Centers need powerful solutions for data classification and redaction to ensure compliance and safeguard sensitive information. Ontelio's Censori automates the identification and classification of sensitive data, drastically cutting down manual efforts and minimizing human error. Censori's consistent labeling and tagging system provides clear data sensitivity understanding across your organization, while its real-time inventory maintenance ensures ongoing compliance and security. Additionally, Censori integrates with existing access control systems, allowing for detailed access controls based on data classification, thus bolstering the protection of sensitive data.
Censori streamlines data mapping, allowing organizations to effectively track and safeguard personal and sensitive data. Its automated redaction process aligns with regulations requiring data anonymization or pseudonymization, and the comprehensive audit trail it maintains is invaluable for regulatory reporting and compliance audits. With Censori, Contact Centers can achieve enhanced data protection, realize time and cost efficiencies, and maintain regulatory compliance. This fortifies reputation management, as protecting sensitive information and meeting regulatory standards builds trust with customers, partners, and stakeholders – a vital element in today's data-focused business landscape.

Today organizations face constant pressure to safeguard customer information while navigating a maze of regulatory requirements. Compliance is not...

As organizations expand globally, the complexity of managing data privacy across multiple languages and jurisdictions intensifies. Contact centers...

Contact centers must efficiently manage vast amounts of customer interactions while ensuring compliance with strict data privacy regulations. AI...